Cyber Manhunt
- Loading...
- Loading...
- Loading...
- Loading...
- Loading...
- Loading...
Cyber Manhunt Preisvergleich
Cyber Manhunt PC
- PlatformSteam
- TypeGift
- VersionsGLOBAL
Kann aktiviert werden in: RumänienANGEBOTE VON 1 VERKÄUFERN12.47 USDCyber Manhunt PC
- PlatformSteam
- TypeGift
- VersionsEUROPE
Kann aktiviert werden in: RumänienANGEBOTE VON 1 VERKÄUFERN10.25 USD10.35 USDCyber Manhunt PC
- PlatformSteam
- TypeGift
- VersionsNORTH AMERICA
Kann nicht aktiviert werden in: RumänienANGEBOTE VON 1 VERKÄUFERN12.47 USDCyber Manhunt PC
- PlatformSteam
- TypeGift
- VersionsJAPAN
Kann nicht aktiviert werden in: RumänienANGEBOTE VON 1 VERKÄUFERN9.02 USD10.35 USDCyber Manhunt PC
- PlatformSteam
- TypeKey
- VersionsGLOBAL
Kann aktiviert werden in: RumänienANGEBOTE VON 8 VERKÄUFER6.76 USD10.35 USDCyber Manhunt PC
- PlatformSteam
- TypeAccount
- VersionsGLOBAL
Kann aktiviert werden in: RumänienANGEBOTE VON 1 VERKÄUFERN14.90 USD
6 aus 6 Artikeln
Über Cyber Manhunt
During the internal communication, we found that when the Internet continues to penetrate people's lives and accelerate the transmission of information, a negative event can quickly spread throughout the Internet. In this process, sin will be exposed and punished, which will make people happy; but some people will suffer malicious insults and insults from the Internet keyboard man.
Cyber Violence
When these cyber violence continue to escalate, the consequences often exceed the incident itself, and even more stressful and end precious lives. Therefore, we decided to develop such a game related to the theme of "hacking", "cyber manhunt" and "privacy data leakage". We hope that players can play the role of a hacker, and find out their privacy secrets, like God controls the destiny of others behind his back and witnesses their end. I hope that through this process, players can think and make their own right judgments.
Gameplay
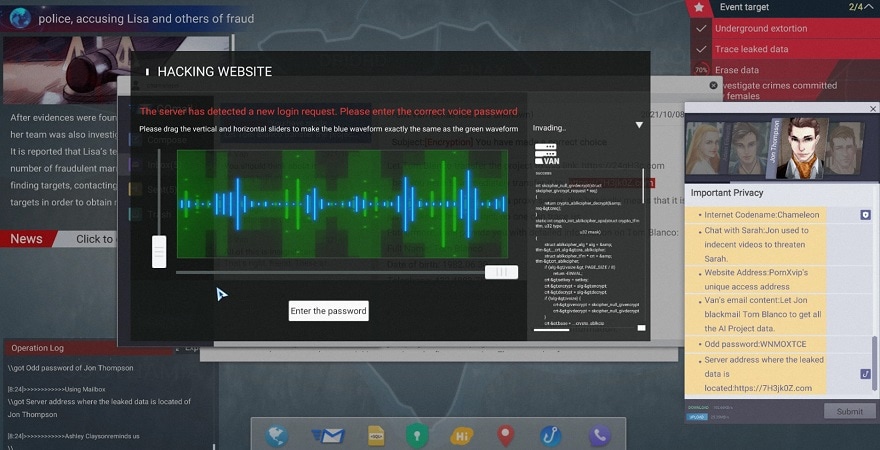
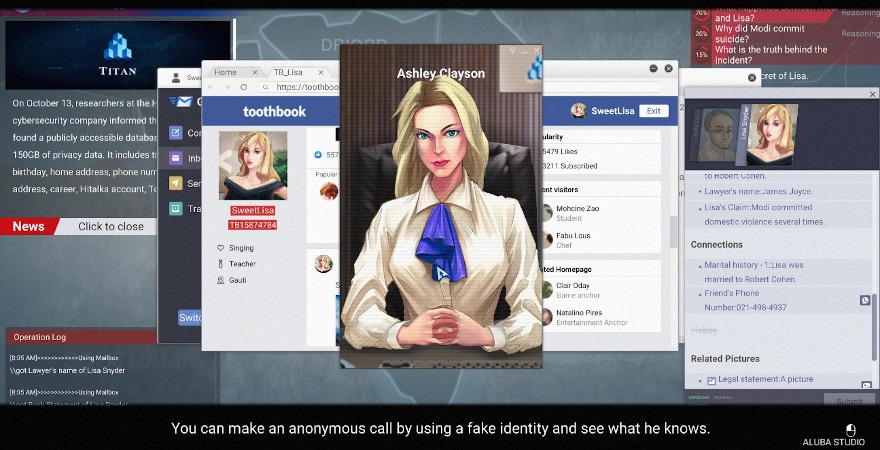
The player plays a hacker in the game, accepts the commission of a company, and completes cyber manhunt incidents. There are a lot of Social Engineering features in the game, also include Reasoning, Tracking, Puzzles-Solving, Destroying and Invading etc. The game will judge the good and evil of the player's behavior. Different judgments will trigger the corresponding plot direction. There are many characters on the stage who has its own personality characteristics and unknown stories. You play a hacker to discover the truth of the incident one by one.
Key Features
- Web search - The player collects basic information about the target object through the browser search function.
- Database - Use known information to enter into the database. After filtering, perhaps other information about the target object.
- Crack - Generate passwords based on the obtained target person information, and use it to log in to accounts on various platforms
- Disguise - Obtain the needs, social circles, etc. of the target object
- Chat Routine - After adding the target object as a friend, perform a chat Routine to get information.
- Picture Analysis - Get valuable information and relevant clues from pictures.
- Phishing - Send phishing links to invade the target person's hardware devices (computer, mobile phone), and obtain private information.
Bewertungen
Schau dir an, was unsere Kunden von diesem Titel haltenEs sind noch keine Bewertungen für diesen Artikel vorhanden
Füge eine Bewertung hinzu und erhalte einen 5 % Rabatt für deinen nächsten EinkaufMelde dich für unseren Newsletter an und hol dir 11 % Rabatt
Abonniere, um Updates zu bekommen, bestätige dein Abonnement,
und hol dir einen Rabattcode, den du sofort nutzen kannst
G2A.COM Limited (Plattformbetreiber)
Adresse: 31/F, Tower Two, Times Square, 1
Matheson Street
Causeway Bay, Hongkong
Handelsregisternummer: 63264201
G2A LLC (Plattformbetreiber)
Adresse: 701 South Carson Street, Suite 200,
Carson City, Nevada 89701,
Nevada 89701, USA
Handelsregisternummer: E0627762014-7
G2A.COM Direct B.V. (Plattformunterstützung)
Adresse: James Wattstraat 77 A 3
1097DL Amsterdam, Niederlande,
Handelsregisternummer: 89975561
Durch die Nutzung der G2A.COM-Plattform erklärst du dich mit den G2A-Nutzungsbedingungen einverstanden. Informationen darüber, wie wir deine personenbezogenen Daten verarbeiten, findest du in der Datenschutz- und Cookie-Richtlinie. Copyright © G2A Group. Alle Rechte vorbehalten.